Difference between revisions of "M2MBridge Functionality"
From AMTech WikiDocs
| Line 2: | Line 2: | ||
**SNMP, LLRP, iBeacon, eddystone, PLC, GPIO, EPC and many others proprietary protocols | **SNMP, LLRP, iBeacon, eddystone, PLC, GPIO, EPC and many others proprietary protocols | ||
* Device-to-device or device-to-cloud communications (connecting the devices to the cloud) | * Device-to-device or device-to-cloud communications (connecting the devices to the cloud) | ||
| − | **[https://www.lora-alliance.org/ LoRa], wifi, classic Bluetooth, BLE, [http://www.wi-fi.org/discover-wi-fi/wi-fi-halow Wi-Fi HaLow], ZigBee, [http://www.link-labs.com/symphony/ Symphony Link] | + | **[https://www.lora-alliance.org/ LoRa], wifi, classic Bluetooth, [https://www.bluetooth.com/what-is-bluetooth-technology/bluetooth-technology-basics/low-energy BLE], [http://www.wi-fi.org/discover-wi-fi/wi-fi-halow Wi-Fi HaLow], ZigBee, [http://www.link-labs.com/symphony/ Symphony Link] |
* Centralized administration of IoT devices and gateways. | * Centralized administration of IoT devices and gateways. | ||
**Centralized configuration information at startup and real time modifications | **Centralized configuration information at startup and real time modifications | ||
Revision as of 14:21, 30 April 2016
- Integrated devices and M2M protocols (data and commands from/to devices)
- SNMP, LLRP, iBeacon, eddystone, PLC, GPIO, EPC and many others proprietary protocols
- Device-to-device or device-to-cloud communications (connecting the devices to the cloud)
- LoRa, wifi, classic Bluetooth, BLE, Wi-Fi HaLow, ZigBee, Symphony Link
- Centralized administration of IoT devices and gateways.
- Centralized configuration information at startup and real time modifications
- Configurable edge intelligence
- Configurable auto-discover
- Implements common functionality and orchestrates the execution of the protocols
- Network failure detection and recovery
- Security
- Access control policies to manage observation production and consumption
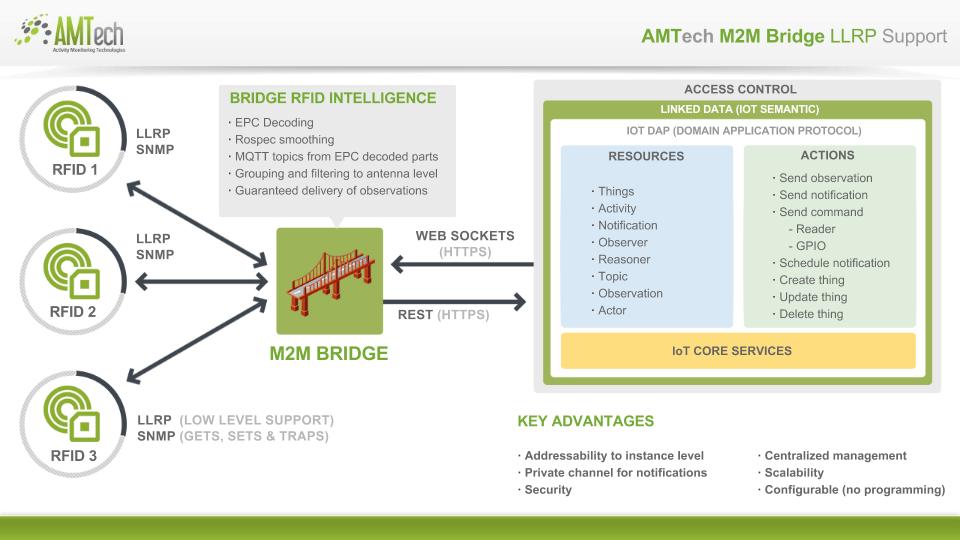
- The following diagram illustrates a M2MBrdige configuration:
- Using LLRP protocol to get the data from EPC tags and send commands to the reader
- Using SNMP to monitor the health o the readers
- Using smoothing, decoding, grouping, access control and other edge intelligence